11-05-13 | Blog Post
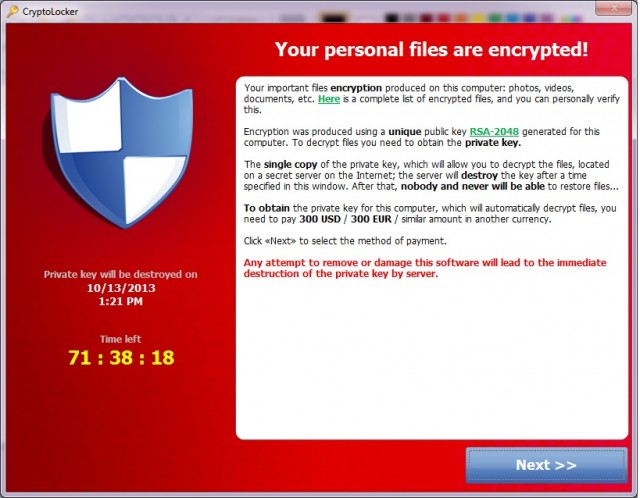
Malware with a business plan – that’s how I’d describe Cryptolocker, the latest encryption-turned-bad software to hit PCs. Categorized as ‘ransomware,’ this type of malware encrypts files on your computer and refuses to decrypt until you pay the malware authors a fee. What’s worse is the threat of permanent deletion if you don’t pay – the malware displays a countdown timer that shows you how long you have to pay up until your files are gone forever, as ThreatTrackSecurity.com reports. This malware is delivered via email attachments.
According to PCWorld.com, Cryptolocker uses public-private key cryptography to encrypt files, and it’s impossible to decrypt without the keys they hold. After your time is up (72 hours), the unique decryption key for the files are automatically destroyed. All they ask for is 300 USD/EUR. You can even pay in Bitcoin. They also take payment via MoneyPack, a prepaid card. Arstechnica.com reports that Symantec estimates their haul to be over $5 million a year.
Their latest service gives you another option if your antivirus detects the malware after files are encrypted and deletes the malware before you were able to buy the decryption keys – however, this takes a bit longer for them to recover your data and is much more costly – it’ll run you about 10 Bitcoins. This is because they need to search for an associated private key and run a brute force attack against themselves in order to find a stored private key that will unlock your data, as Paul Ducklin from Sophos reports.
How can you protect yourselves from ransomware? Back up your data regularly and have a solid IT disaster recovery plan in place. Better yet, encrypt your backups as they’re archived and locate them in an offsite data center. Sending data offsite ensures a copy of your critical data is available in the event of a disaster at your primary site, and it is considered a best practice.
Here are some tips from our Disaster Recovery white paper about outsourcing offsite backup and why it might be a good option to protect against malware that takes your data hostage:
Outsourcing your offsite backup to a managed services provider can provide your organization with continuous data protection and full file-level restoration, and offload the burden of installing, managing, monitoring as well as complete restoration after a disaster.
With a vendor, your encrypted server files are sent to an onsite backup manager (primary site), which are then sent to a secondary, offsite backup manager, ideally far enough apart to reduce the chances of the secondary site being affected by the same disaster or interruption.
While offsite backup managed in-house can be costly due to building out, maintaining and upgrading both primary and secondary sites, outsourcing your offsite backup to professionals means you can take advantage of their investments in capital, technology and expertise.
As NIST (National Institute of Science and Technology) states, backup media should be stored offsite or at an alternate site in a secure, environmentally controlled facility. An offsite backup data center should have physical, network and environmental controls to maintain a high level of security and safety from possible backup damage.
References:
CryptoLocker creators try to extort even more money from victims with new service
Cryptolocker: Time to Backup
CryptoLocker ransomware crooks offer “late payment penalty” option
You’re infected—if you want to see your data again, pay us $300 in Bitcoins